Policy Enhancements
- Home
- Single Service
- Partner Enhancements



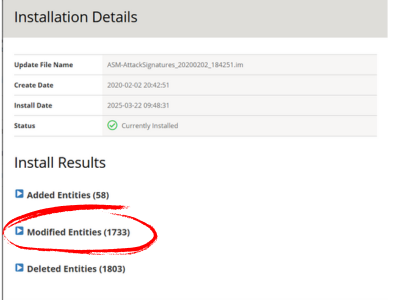
About the ASM Attack Signature Updates
Are your F5 ASM ADC signatures not being updated regularly, or worse, years out of date altogether? You're not alone.
In most cases, it comes down to a lack of ASM-specific skills, which leads to low confidence and hesitation. Past update attempts may have caused unexpected behaviour or downtime, and once that happens, application owners lose trust in the F5 ASM/WAF.
Signature updates are often considered risky, time-consuming, or too much effort, so they are not part of the F5 ADC BAU tasks.
But the truth is that policies rely heavily on up-to-date signatures across all scopes to defend against modern vulnerabilities. Without them, your ASM/WAF is doing its best with outdated information, and your applications are seriously exposed.
Regular, safe updates restore confidence. You get the protection that works, and app owners sleep at night knowing the application is protected by up-to-date F5 ASM Signatures.
Don't leave your apps vulnerable to attacks, hacks, or penetration just because a routine procedure is missed. A signature update is simple—the risk of skipping it is not.
Important Facts
- Out of Date Signatures, Applications are Exposed
- Signatures protect all scopes of the Application
- Set up correctly, this is a Safe Process
- Monitor through the ERP until Enforcement
- Adjustments and Entity overrides where Needed
- Adjustment for possible Automation
- Next Steps, This is a Monthly Process
