Expert F5 ASM / WAF Management, Production Expertise Your Applications Need
Managing an F5 ASM policy well isn't about watching traffic all day. It's about understanding what is required, knowing exactly when to act and what to look for when you do.
We bring to your applications 15 years of production F5 ASM experience, along with 30+ years of production development skills, to deliver expert-level application security at a fraction of the cost.
No commitment. 30-minute call to assess your current F5 ASM/WAF posture.
World-class application security for a fraction of what you pay today for average. We keep your policies and attack signatures current, staged, and fully integrated, protecting your applications from both known vulnerabilities and zero-day threats.
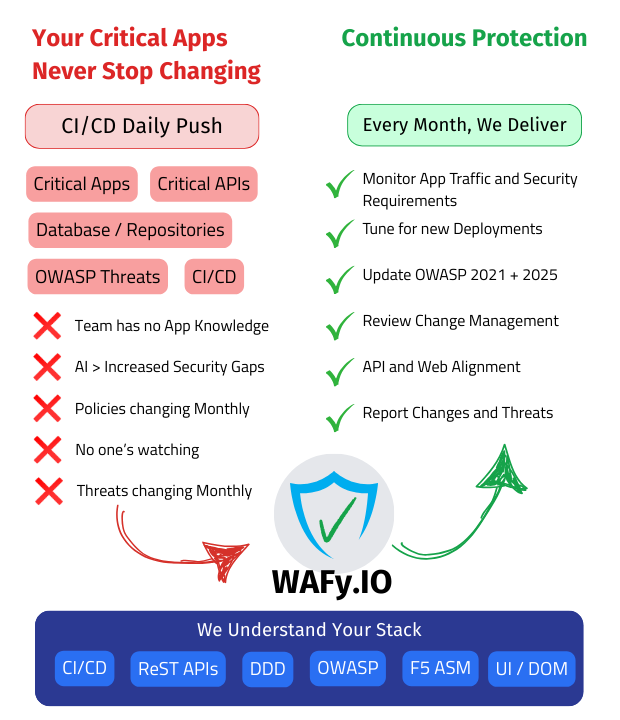
Most ASM Policies We Inherit Aren't Where They Should Be
It's very common. Policies were deployed with good intentions, but over time, they've drifted. Signatures/Entries left staged. Learning suggestions have gone unreviewed for months. Entities are either too loose or generating false positives that nobody has time to investigate. Many policies are still sitting in transparent mode, logging attacks but not blocking them.
WAFy starts by assessing exactly where your ASM/WAF policies are today and building a clear plan to bring them to production-grade standards aligned with the OWASP Top 10 (2021) and Top 10 (2025).
Every change we make is in your live production environment, that's where real WAF management happens. We follow your change management process, document every change, and observe the impact under real traffic before taking the next step. We don't rush enforcement. We follow a well-understood process of updating and staging everything.
Managed F5 ASM, from First Policy to Full Enforcement
WAFy delivers hands-on F5 ASM policy management through every phase of the policy lifecycle. We configure, observe, tune, and tighten, working with your real application traffic to build policies that genuinely protect your environment.
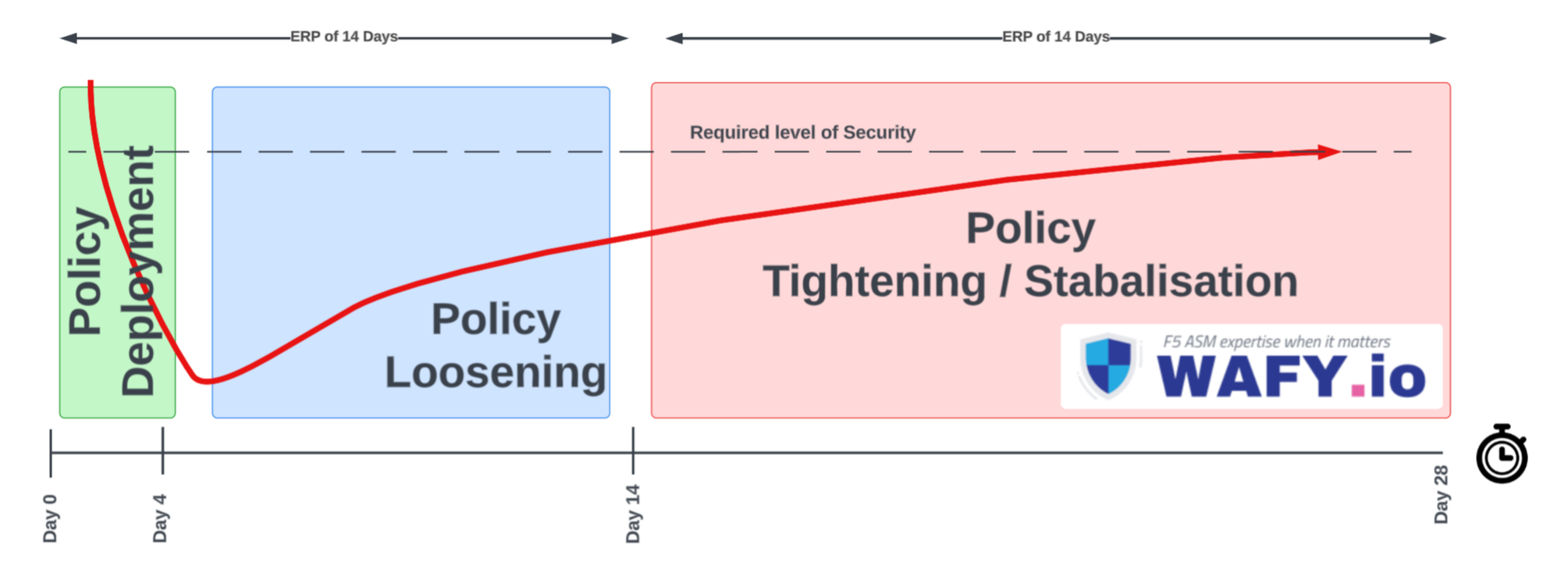

Loosen & Establish
We design and deploy OWASP Top 10 (2021) aligned ASM policies tailored to your applications and traffic patterns. The initial phase is deliberately open — allowing the policy to learn from real traffic while we establish accurate baselines for entities, parameters, and URLs.

Tighten & Tune
As traffic patterns become clear, we progressively tighten enforcement. Learning suggestions are reviewed, false positives are addressed, attack signatures are staged, and entity configurations are refined. Each change is observed under real traffic before the next adjustment is made.

Adjust & Maintain
Once policies reach blocking mode, the ongoing work shifts to monthly reviews, signature updates, learning suggestion checks, fine-tuning for application changes, and compliance reporting. Your policies stay current and accurate as your applications evolve.
Join Our Free Newsletter
Packed full of F5 ASM Updated, important and Critical Information, as well as configuration tips and learning.
Choose Your Service Level.
Why Organisations Choose WAFy
WAFy delivers hands-on F5 ASM policy management through every phase of the policy lifecycle. We configure, observe, tune, tighten, and stabilise working with your real application traffic to build policies that genuinely protect your environment and applications.
Production Experience, Not Lab Theory
15 years of F5 ASM deployments across banking, aviation, insurance, and government. Every policy decision we make comes from real production experience with real traffic.
F5 401 Certified
Your WAF is managed by an F5 Certified Technology Specialist (Security), the highest F5 security certification available. Not a junior analyst following a runbook.
Retained Context
We maintain full documentation of your environment, policies, and decisions. Pause your subscription and return anytime; we pick up exactly where we left off. No re-onboarding, no lost knowledge.
Transparent Reporting
Monthly reports covering policy accuracy, signature updates, false positive trends, and progress toward blocking mode. You always know exactly where your WAF security stands.
Getting Started Takes One Call
Book a 30-minute discovery call. We'll assess your current ASM posture and give you a clear picture of where your policies stand, whether you engage us or not.
Book a Discovery Call
Is this a replacement for our F5 support contract?
Do we need to give you access to our F5 devices?
What if we already have ASM policies deployed?
Can we pause and resume the service?
What's the minimum commitment?
How is WAFy different from Approxee?
How do we know you can deliver what you promise?

Core Financial
Progressed ASM policies from transparent to blocking mode across production internet banking communication applications

Aviation
Managed WAF policies protecting passenger-facing booking and staff systems and Aviation manufacturing facilities.

Insurance
Delivered OWASP-aligned ASM policy remediation across legacy and modern application estates. Working with Legacy means legacy OWASP issues

Petrochemical
Supported WAF policy compliance requirements in regulated Government sector environments. There were mainly internal private apps.
Join Our Free Newsletter
Packed full of F5 ASM Updated, important and Critical Information, as well as configuration tips and learning.
WAFy.IO is designed by Graham Mattingley, F5 401 Certified Technology Specialist and developer (Security) | An Approxee Ltd Service

